Deploying 20 times a day while staying SOX compliant? It’s not just possible – it’s the competitive advantage your organization needs.
Speed kills compliance.
At least, that’s what most finance teams think when developers push code 20 times a day. But here’s the reality: organizations can deploy faster AND stay compliant with SOX regulations. They just need the right change monitoring framework.
DevOps transformed how software ships. Automation replaced manual handoffs. CI/CD pipelines cut deployment times from weeks to minutes. But for publicly traded companies and financial institutions subject to Sarbanes-Oxley (SOX) requirements, this velocity creates a massive challenge: how do teams maintain strict controls, complete documentation, and full auditability without grinding innovation to a halt?
If you’re a DevOps leader, compliance officer, or CTO at a regulated company, you’re facing this exact dilemma. Your developers want speed. Your auditors demand control. Your business needs both.
The answer lies in intelligent change monitoring. A system that tracks, validates, and audits every change throughout the DevOps pipeline while keeping deployment velocity high.
This guide breaks down exactly how to build SOX-compliant DevOps processes that accelerate delivery instead of slowing it down.
Change Monitoring Risks in SOX Compliance: 4 Critical Challenges
Most teams think they’re compliant until the auditors show up. Then reality hits: gaps in change tracking, missing approval records, and zero audit trails. These risks compound quickly in fast-moving DevOps environments.
The cost of getting this wrong? Failed audits, regulatory fines, damaged reputation, and weeks of remediation work that brings development to a standstill. Let’s examine the four critical vulnerabilities that put your organization at risk.
1. Zero Visibility Into Production Changes
The problem starts when developers push changes directly to production, bypassing version control, skipping code reviews, and leaving no trace in audit logs.
What goes wrong:
- No centralized log showing what changed, when, and by whom
- Emergency hotfixes deployed without documentation
- Rollbacks become guesswork because nobody knows the last stable state
- Incident response takes 3x longer without change history
When auditors request change logs for Q4 deployments, teams scramble to reconstruct history from Slack messages and memory. That’s an automatic compliance failure.
2. Manual Approval Processes That Don’t Scale
Approvals handled through email chains, Slack threads, or verbal sign-offs create massive compliance gaps.
The real cost:
- Inconsistent approval standards across teams and environments
- No timestamps or digital signatures for audit trails
- Bottlenecks that delay critical deployments by days
- Approvers who rubber-stamp changes without reviewing
Manual processes might work for five deployments per month. At 500 deployments, they collapse completely, taking compliance with them.
3. Missing Segregation of Duties (SoD)
SOX mandates that the person writing code cannot approve their own changes or deploy to production. But in many DevOps environments, developers have unrestricted access to do exactly that.
Why this matters:
- Single individuals can introduce and deploy malicious or broken code
- No checks and balances between development, review, and deployment
- Auditors flag SoD violations immediately, often triggering deeper investigations
- Internal controls fail when one person controls the entire pipeline
The “move fast” mentality can’t override fundamental compliance requirements. Organizations need technical controls that enforce SoD automatically.
4. Unclear Change Ownership and Accountability
When something breaks in production, teams need to know immediately: who deployed it, what changed, and which approver signed off. Without clear ownership, incident response stalls.
Common scenarios:
- Multiple developers pushing to the same repository without coordination
- Changes merged and deployed with generic commit messages like “fixed bug”
- No connection between tickets, code commits, and production deployments
- Finger-pointing during incidents because accountability isn’t documented
Establishing ownership isn’t about blame. It’s about speed. Teams that track ownership resolve incidents 60% faster than those that don’t.
Understanding these risks is the first step. Now let’s explore proven strategies that eliminate these vulnerabilities while maintaining deployment velocity.
Best Practices for SOX Compliance in DevOps: 8 Proven Strategies
Compliance doesn’t require sacrificing velocity. The best-performing teams achieve both by embedding controls directly into their DevOps workflows. These practices deliver speed AND auditability.
1. Version Control Everything (Not Just Code)
Treating infrastructure and configuration the same as application code creates a single source of truth for all system changes.
What to version control:
- Application source code (obviously)
- Infrastructure as Code (IaC) templates: Terraform, CloudFormation, Ansible playbooks
- Configuration files, environment variables, and secrets management policies
- Deployment scripts, CI/CD pipeline configurations
- Documentation and runbooks
Why this works: Every change gets a commit hash, timestamp, and author attribution. Code reviews become mandatory through pull request workflows. Rollbacks become simple git reverts. Auditors get complete change history with one command: git log.
Implementation tip: Require all changes to go through Git with no exceptions. Disable direct server access. If someone needs emergency production access, document it in a ticket and provide temporary credentials that expire after 4 hours.
2. Build CI/CD Pipelines With Immutable Logs
Automated pipelines create consistency and comprehensive audit trails that manual processes can never match.
Essential pipeline features:
- Automated build, test, security scan, and deploy stages
- Timestamped logs for every pipeline execution (successful or failed)
- Integration with centralized logging (CloudWatch, Splunk, Datadog)
- Deployment receipts showing exactly which code version went to which environment
Critical detail: Make pipelines the ONLY way to deploy to production. When Bitcot implements CI/CD solutions for financial services clients, the first step is always to disable manual deployment access. If the pipeline is down, production doesn’t get updates. Period.
Understanding the DevOps Infinity Loop helps teams visualize how continuous integration and deployment creates a seamless feedback cycle from planning through monitoring.
Want to learn more about building robust CI/CD systems? Check out our guide on 15 Best CI/CD Tools Every Business Needs and DevOps Techniques to Speed Up Your CI/CD Workflow.
3. Implement Automated Approval Gates
Approval gates enforce mandatory review before changes hit production without creating deployment bottlenecks.
How to design approval gates:
- Low-risk changes (documentation updates): peer review only
- Medium-risk changes (feature additions): peer review + automated security scan
- High-risk changes (database migrations): peer review + manager approval + change advisory board
Key implementation details:
- Use tools like GitHub Actions, GitLab CI, or Azure DevOps with built-in approval workflows
- Store approval records with cryptographic timestamps
- Configure automatic approvals for validated test deployments while requiring human approval for production
- Set approval expiration. A manager’s approval from Monday doesn’t validate Friday’s significantly different change
4. Create Tamper-Proof Audit Logs
Audit logs must be immutable, centralized, and easily searchable. If logs can be modified or deleted, they’re worthless for compliance.
What immutable logging looks like:
- Store logs in write-once-read-many (WORM) storage like AWS S3 with Object Lock
- Use AWS CloudTrail or equivalent for API-level auditing
- Implement log aggregation tools that prevent deletion by application admins
- Retain logs for 7+ years per SOX requirements (verify your specific retention policy)
What to log:
- Every deployment: who initiated it, which commit, which environment, timestamp
- All approval actions: who approved, when, which change request
- Failed deployments and rollbacks
- Manual interventions or emergency access grants
5. Link Every Change to a Tracking Ticket
Tickets create accountability and context. They connect business requirements to code changes to production deployments, creating an audit trail auditors actually want to see.
Effective ticketing practices:
- Create Jira/ServiceNow tickets for every change: features, bugs, infrastructure updates, security patches
- Include: change description, affected systems, risk assessment, approvers, rollback plan
- Link tickets to Git commits using commit message conventions: [JIRA-1234] Fix authentication bug
- Link tickets to CI/CD deployments automatically
- Require ticket references in merge requests and block merges without them
Why this matters: When auditors ask “show me all infrastructure changes in Q3,” teams can pull a Jira report in 30 seconds instead of reconstructing history from scattered sources.
6. Document Change Management Policies in Living Documents
Written policies prove to auditors that controls exist, but they need to reflect actual practices, not aspirational ones.
What to document:
- Step-by-step change approval workflows with decision trees
- Roles and responsibilities: who can approve what types of changes
- Emergency change procedures with required notifications
- Rollback procedures for different failure scenarios
- Diagrams showing the path from code commit to production deployment
Pro tip: Keep policies in Git alongside infrastructure code. Update them as processes evolve. Review quarterly with teams to ensure documentation matches reality.
7. Enable Real-Time Monitoring and Anomaly Detection
Detecting unauthorized changes in real time prevents compliance violations before they become audit findings. Continuous monitoring catches issues early and enables faster incident response.
Monitoring essentials:
- AWS GuardDuty, Azure Security Center, or Google Cloud Security Command Center for cloud infrastructure
- CloudTrail monitoring with alerts for suspicious API calls
- Configuration drift detection (AWS Config, Azure Policy)
- Alerts for direct production changes that bypass pipelines
- Dashboard visibility into all environment changes across the organization
Alert on:
- Production deployments outside approved time windows
- Changes made by accounts that shouldn’t have production access
- Infrastructure modifications without corresponding tickets
- Multiple failed deployment attempts suggesting possible issues
8. Audit Access and Permissions Quarterly
People change roles, contractors leave, responsibilities shift. Access permissions need regular review to maintain least privilege and segregation of duties.
Quarterly access review checklist:
- GitHub/GitLab repository permissions and branch protection rules
- Cloud IAM roles and service account permissions
- CI/CD tool access (who can edit pipelines, approve deployments)
- Production environment access (SSH keys, database credentials)
- Remove all access for departed team members immediately and automate this process with HR system integration
Automation opportunity: Use tools like AWS Access Analyzer or Azure AD Access Reviews to flag over-permissioned accounts automatically. Don’t rely on manual spreadsheets. They’re always outdated.
Modern AI automation tools can also help identify access anomalies and automate compliance reporting, reducing the burden on security teams.
Need help implementing these practices in your organization? Get in touch with our DevOps consulting team. We specialize in building compliant CI/CD pipelines for regulated industries.
These eight practices form the foundation of SOX-compliant DevOps. But implementation isn’t just about checking boxes. It’s about transforming how teams work. Here’s what organizations actually gain when they get change monitoring right.
Benefits of SOX-Compliant Change Monitoring for DevOps Teams
Organizations that implement proper change monitoring don’t just pass audits. They build better systems that ship faster and break less often. The benefits compound across the entire development lifecycle.
Incident Response That’s 3x Faster
Complete change history transforms how teams troubleshoot production issues.
The difference:
- Before: “Production is down. Nobody knows what deployed last.” 2 hours of detective work
- After: Check the audit log, see the 14:32 deployment, review the exact code change, roll back in 8 minutes
Teams save massive amounts of time by eliminating the “what changed?” investigation. Every incident starts with a clear timeline of recent changes, narrowing the root cause search immediately.
Accountability That Actually Changes Behavior
When every change is traceable to a specific person, ticket, and approval chain, teams become more deliberate about what they deploy.
Observable patterns:
- Developers write better commit messages because they know auditors will read them
- Reviewers actually review code instead of rubber-stamping because their approval is recorded
- Teams test more thoroughly before production deployments
- Reckless “cowboy deployments” disappear when there’s a clear audit trail
Transparency doesn’t slow teams down. It makes them more professional.
Change Management That Doesn’t Create Bottlenecks
Automated approval workflows process standard changes in minutes while flagging high-risk changes for additional review.
How this works:
- Configuration updates: automated approval → production in 15 minutes
- Feature releases: peer review → automated testing → production in 1 hour
- Database schema changes: peer review → DBA approval → manager sign-off → scheduled maintenance window
Clear policies eliminate confusion about which changes need which approvals. Teams stop waiting for clarification and start shipping.
Security Posture That Catches Problems Early
Change monitoring surfaces security issues before they become incidents.
Real examples:
- Alerts flag when developers commit AWS keys to repositories
- Automated scans catch vulnerable dependencies before production deployment
- Monitoring detects configuration drift that could expose systems
- Access reviews identify over-permissioned accounts before they’re exploited
Prevention is cheaper than incident response. Organizations with strong change monitoring typically see 60-70% fewer security incidents related to misconfigurations or unauthorized changes.
The choice is clear: implement proper change monitoring now, or face the mounting costs of compliance failures, security breaches, and operational chaos later.
While these benefits are compelling today, the future of SOX-compliant DevOps is evolving rapidly. Let’s examine the emerging trends that will reshape compliance in 2026 and beyond.
Emerging Trends: The Future of SOX-Compliant DevOps in 2026
The DevOps compliance landscape is evolving rapidly. While core SOX requirements remain constant, the technologies for meeting them are transforming. Organizations that embrace these trends will maintain compliance while dramatically improving velocity and security.
1. AIOps: Intelligent Compliance Automation
By 2026, AI for IT Operations (AIOps) is becoming essential for compliance at scale, with the market expected to grow at roughly 15% annually.
How AIOps Transforms SOX Compliance:
- Automated Anomaly Detection: Machine learning analyzes deployment patterns and access logs to detect compliance violations in real time instead of waiting for quarterly audits
- Predictive Risk Scoring: AI predicts which changes carry highest SOX violation risk, automatically triggering additional approval requirements
- Intelligent Alert Reduction: Filters noise by clustering related alerts, preventing alert fatigue while ensuring genuine violations receive immediate attention
- Autonomous Remediation: Automatically reverts unauthorized configuration changes and logs incidents, maintaining compliance without manual intervention
Implementation for SOX:
- Deploy tools like AWS DevOps Guru, Datadog AIOps, or Splunk IT Service Intelligence
- Train ML models on your organization’s historical compliance data
- Maintain human oversight for high-impact compliance actions
- Document AI decision-making logic for auditor review
Critical Balance: While AIOps provides powerful automation, always validate AI recommendations against SOX requirements and maintain human review for critical compliance decisions.
2. Platform Engineering: Centralized Compliance Controls
Gartner expects around 80% of engineering organizations to have platform engineering teams by 2026. This approach centralizes compliance controls into Internal Developer Platforms (IDPs) that automatically enforce SOX requirements.
Key Compliance Benefits:
- Golden Paths with Built-In Controls: Pre-approved deployment pipelines with mandatory approval gates, automatic audit logging, and built-in segregation of duties
- Consistent Policy Enforcement: Security and compliance policies apply uniformly across all teams because controls exist at the platform level, not per-team
- Self-Service Within Guardrails: Developers deploy rapidly through self-service portals but cannot bypass audit logging, approval workflows, or access controls
Implementation Strategy:
- Start with a minimal viable platform solving biggest compliance pain points
- Build in observability and audit logging from day one
- Implement policy-as-code to enforce SOX requirements automatically
- Use tools like Backstage, Humanitec, or AWS Proton for orchestration
3. Enhanced Cybersecurity Integration
SOX compliance now encompasses comprehensive cybersecurity frameworks. Cybersecurity controls are being evaluated alongside traditional IT controls during SOX testing, with SEC enforcement making cybersecurity a central compliance pillar.
What’s Changing:
- Cyber Controls as Financial Controls: SEC expects cybersecurity risks assessed as rigorously as financial reporting risks
- DevSecOps Foundation: Security integrated throughout the software development lifecycle via CI/CD pipelines
- Shift Security Left: SAST, DAST, SCA, and secret scanning prevent vulnerabilities before production
- Zero-Trust for Financial Systems: Every access request requires verification and logging for audit purposes
- Continuous Monitoring: Real-time policy enforcement for compliance frameworks rather than periodic assessments
4. Multi-Cloud Compliance Management
By 2026, over 75% of organizations will adopt multi-cloud or hybrid strategies, creating new compliance challenges across AWS, Azure, and GCP.
Solutions:
- Unified Compliance Platform: Tools like CloudHealth or Prisma Cloud provide consistent monitoring across all cloud providers
- Policy-as-Code: Use Open Policy Agent (OPA) to define SOX policies once and enforce everywhere
- Centralized Audit Aggregation: Single log platform (Splunk, Datadog) that normalizes audit data from all clouds
- Cloud-Agnostic IaC: Terraform or Pulumi makes compliance controls portable across providers
5. ESG and Non-Financial Data Controls
More public companies are incorporating ESG data into SOX programs, requiring financial reporting controls over non-financial data like carbon emissions and diversity statistics.
For DevOps Teams: Apply the same version control, approval workflows, and audit logging to ESG data pipelines as you would to financial systems. Track changes to ESG calculation methodologies with the same rigor as financial calculations.
Preparing for 2026
These trends are actively reshaping SOX compliance in DevOps. Organizations that embed AI, platform engineering, and enhanced security into compliance frameworks today will lead competitors still using traditional approaches.
Action Steps:
- Assess which trends your organization has adopted
- Prioritize AIOps and platform engineering for biggest impact
- Start with pilot projects, not organization-wide transformations
- Track metrics like incident response time and deployment frequency
- Plan quarterly reassessments as technologies evolve rapidly
These trends point toward the future, but successful implementation requires a systematic approach today. Use this comprehensive checklist to evaluate your current DevOps environment and identify specific gaps in your SOX compliance strategy.
Overwhelmed by the scope of changes needed? You don’t have to do this alone. Partner with experienced DevOps consultants who can assess your current state and create a phased implementation roadmap.
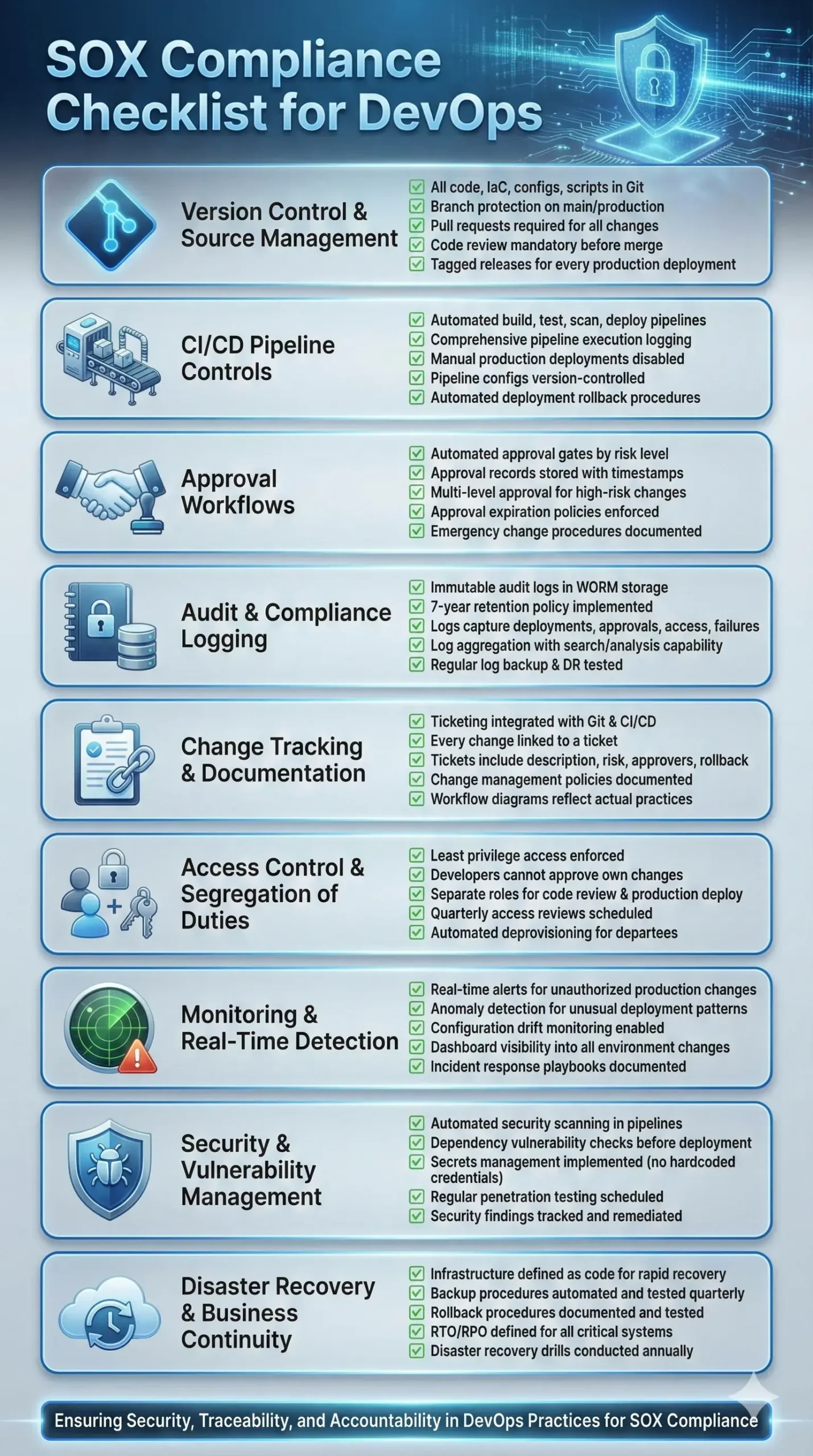
SOX Compliance Checklist for DevOps: Complete Implementation Roadmap
Use this checklist to evaluate current practices and identify gaps:
With these frameworks in place, DevOps teams can deliver at high velocity while maintaining the controls necessary for SOX compliance. But knowing what to do and actually implementing it are two different challenges. Here’s what it takes to make this transformation real.
Final Thoughts: Balancing Speed and Compliance in Modern DevOps
The companies winning at DevOps aren’t choosing between velocity and compliance. They’re embedding compliance into velocity. Every automated pipeline, approval gate, and audit log becomes part of the infrastructure that enables faster, safer deployments.
Change monitoring isn’t a regulatory burden teams reluctantly carry. It’s the foundation for building systems that ship confidently, recover quickly, and maintain integrity under pressure.
The key insight: Compliance controls done right don’t slow teams down. They eliminate the chaos that ACTUALLY slows teams down. Clear ownership, automated workflows, and comprehensive audit trails reduce confusion, prevent errors, and accelerate incident response.
Without proper change monitoring, you’re risking:
- Failed SOX audits and regulatory penalties
- Security breaches from unauthorized changes
- Extended downtime during incidents (2+ hours vs. 8 minutes)
- Developer frustration and reduced productivity
- Loss of competitive advantage to more agile competitors
With SOX-compliant change monitoring, you achieve:
- Audit-ready documentation that passes inspection every time
- 3x faster incident response and resolution
- 60-70% reduction in security incidents
- Confident, rapid deployments without compliance fear
- A competitive edge through regulated innovation
Ready to Transform Your DevOps Compliance?
For organizations ready to transform their DevOps practices with proper change monitoring and compliance frameworks, our DevOps consulting services help companies build CI/CD pipelines that balance speed with control. With proven methodologies and deep expertise in regulated industries, Bitcot enables teams to deploy faster while meeting the strictest compliance requirements.
Our approach includes:
- Comprehensive compliance assessment and gap analysis
- Custom CI/CD pipeline design with built-in SOX controls
- AI-powered automation for monitoring and anomaly detection
- Team training on compliant DevOps practices
- Ongoing support for audit preparation and remediation
Organizations can also leverage AI-powered automation to streamline compliance workflows and reduce manual oversight while maintaining audit-ready documentation.
Don’t let compliance fears slow your innovation. Explore more resources on DevOps automation best practices and implementing modern DevOps tools to accelerate your transformation.
Contact Bitcot today to schedule a compliance assessment and discover how we can help you achieve both speed and control in your DevOps operations.