If you’re building in the healthcare space, cloud-based database tools are an incredibly tempting choice. They are fast, scalable, and offer the kind of “snappiness” that modern users expect from a communication app.
But there is a dangerous misconception circulating in many organizations: the idea that because you are using a major tech provider, your application is automatically ready for the strict regulatory demands of the medical industry.
In reality, most real-time platforms don’t provide full regulatory protection “out of the box.” Relying on them to handle Protected Health Information (PHI) without a custom-engineered security layer is a significant business risk. It’s the digital equivalent of building a state-of-the-art clinic but leaving the filing cabinets unlocked in the lobby.
To build a truly healthcare-grade secure messaging platform, you have to bridge the gap between technical speed and legal accountability. Achieving total data adherence isn’t just a “check-the-box” exercise; it requires a shared responsibility architecture.
This means ensuring your infrastructure, your backend logic, and your team’s operational practices all align with federal standards for data safeguarding.
To demonstrate how to overcome these hurdles, we developed a high-performance Proof of Concept (PoC) that solves the “out-of-the-box” gap.
In this deep dive, we’ll explore how we moved beyond the limitations of standard tools to build a platform that doesn’t just send messages; it protects patient trust, satisfies stringent privacy requirements, and secures the future of your business.
What is a Healthcare Secure Messaging Platform?
At its core, a healthcare-grade messaging platform is a communication tool specifically engineered to handle the high-sensitivity environment of medical data.
Unlike standard consumer apps (like WhatsApp or Slack), a healthcare-grade system is built with a “Security First, Feature Second” philosophy.
It serves as a digital bridge between physicians, patients, and administrators, but with three non-negotiable pillars:
- Total Data Sovereignty: Every message, image, and attachment is treated as PHI. The platform ensures that this data is not just encrypted, but that the “keys” to that data stay out of the wrong hands, even the hands of the service provider.
- A Managed Audit Trail: In the medical world, accountability is everything. A secure platform logs every access attempt, modification, and transmission, creating a transparent history that satisfies even the most stringent regulatory audits.
- Identity Certainty: Through multi-factor authentication and role-based access control, the platform ensures that a patient’s lab results are seen only by their specific doctor, preventing the “accidental exposure” risks common in standard chat tools.
In short, it is a protected environment where clinical collaboration can happen at the speed of modern technology without compromising the legal or ethical integrity of the practice.
Many businesses assume that a “secure” consumer app is enough. However, in the medical industry, there is a vast difference between basic encryption and legal adherence.
| Feature | Standard Messaging (e.g., Slack, WhatsApp) | Healthcare-Grade Platform (Our PoC) |
| Legal Accountability | Providers rarely sign agreements for data liability. | Full BAA Support: Infrastructure is legally covered for sensitive data. |
| Data Visibility | Service providers may have access to “metadata” or keys. | Zero-Knowledge Privacy: E2EE ensures only providers and patients see data. |
| Audit Readiness | Basic logs; often lack deep “who/when/where” records. | Comprehensive Audit Trails: Every access event is logged for regulatory review. |
| Identity Control | Simple logins; hard to manage at a clinical level. | Role-Based Access: Permissions mapped to specific clinical duties. |
| Device Security | Data often persists on personal devices indefinitely. | Remote Wipe & Expiry: Admins can clear sensitive data from lost devices. |
While consumer apps are easy to use, they lack the administrative controls required to protect your business during an audit or a data breach. A standard app is a communication tool; a healthcare-grade platform is a protected asset.
By choosing a solution that bridges this gap, your organization doesn’t just “chat”; it builds a defensible, high-trust digital environment that protects both your patients and your bottom line.
Why Standard Firebase Chat Falls Short in Regulated Healthcare
Firebase is widely trusted for building real-time applications, and in many industries, its default security model is more than sufficient.
However, healthcare operates under a very different set of expectations when it comes to data protection, privacy, and accountability.
When Firebase chat is implemented using standard, out-of-the-box patterns, critical gaps emerge, not because the platform is weak, but because regulated healthcare environments demand safeguards that go beyond default configurations.
Below are the key challenges we identified and set out to solve.
Assumed Compliance Creates Hidden Risk
One of the most common issues in healthcare chat implementations is the assumption that using a major cloud-backed platform automatically satisfies regulatory requirements.
But how often is that assumption actually verified?
In reality, compliance is not inherent to the tool; it depends on how services are configured, what data is stored, and how responsibilities are enforced at the application level. When compliance is assumed rather than explicitly designed, organizations face hidden legal and operational risk that often surfaces only during audits, security reviews, or incidents.
In healthcare, assumptions quickly become liabilities.
No Built-In End-to-End Message Encryption
Standard Firebase chat implementations do not provide true end-to-end encryption by default.
While messages are protected during transmission and storage, the message content itself may still be accessible to backend services or system components. For healthcare communication, this creates a privacy gap where sensitive patient conversations are not fully isolated from the infrastructure that stores them.
Without end-to-end encryption, confidential messaging lacks the zero-visibility guarantees expected in regulated environments.
Limited Support for Healthcare-Grade Access Control
Healthcare communication requires strict separation between different user roles, such as administrators, practitioners, and patients.
Out-of-the-box Firebase authentication does not enforce this level of role segregation or provide healthcare-grade Identity & Access Management (IAM) required for sensitive patient.
Without authoritative backend logic, permissions can become overly broad or inconsistent as the application evolves. Over time, this increases the risk of unauthorized access and makes it difficult to demonstrate controlled data access.
Role-based access control must be enforced intentionally, not implied.
Inadequate Default Audit Logging and Monitoring
Regulated healthcare systems require clear visibility into who accessed the system, what actions were taken, and when those actions occurred, without exposing sensitive message content.
Standard Firebase setups do not automatically enforce comprehensive audit logging aligned with these expectations. Without structured logging and monitoring, accountability becomes difficult to prove, and incident investigations become reactive and time-consuming.
When something goes wrong, will you have a clear audit trail, or unanswered questions?
Auditability must be designed as a first-class system feature.
Secure PHI Storage, Retention, and Deletion Requirements
Healthcare chat systems handle PHI, which must be stored, retained, and deleted according to strict data governance rules.
Standard Firebase chat implementations do not provide built-in mechanisms for managing PHI-specific data lifecycles. While Firebase can securely store data, it does not automatically enforce how long sensitive information should be retained, when it must be archived, or how it should be permanently deleted.
Without a structured approach, PHI handling becomes fragmented and difficult to validate, especially as the system grows. Over-retention, improper deletion, or inconsistent enforcement can introduce serious compliance and operational risk.
Patient Consent and Privacy Controls Are Easy to Get Wrong
Managing patient consent is not a one-time action; it is an ongoing enforcement responsibility across the entire system.
In standard implementations, consent logic is often spread across frontend workflows and backend checks, making it difficult to guarantee consistent enforcement. This fragmented approach increases the likelihood of privacy violations and unintended data exposure.
In regulated healthcare environments, even small gaps in consent handling can have serious consequences.
Scaling Without Compromising Compliance is Challenging
Firebase excels at scaling infrastructure, but scaling healthcare communication introduces complexity beyond performance.
As the user base grows:
- Access control becomes harder to govern
- Audit logs grow rapidly
- Encryption and key management become more critical
- Operational oversight becomes more complex
Without a structured compliance-first architecture, growth can introduce risk faster than teams can manage it.
How Bitcot’s PoC Solution Solves the Identified Challenges
To solve the limitations of standard healthcare chat implementations, we deliberately moved away from a “platform-only” mindset and designed a shared-responsibility architecture.
Rather than relying solely on Firebase defaults, our PoC layers security, access control, encryption, and governance across infrastructure, backend logic, and client devices. This ensures sensitive healthcare communication remains protected at every stage, without sacrificing scalability or developer velocity.
At the core of the solution is a zero-knowledge design philosophy: messages are never readable by the system itself.
Our approach recognizes that no single service should be responsible for all aspects of healthcare security.
- Cloud infrastructure ensures regulatory eligibility and baseline security
- Backend services enforce access control, business rules, and governance
- Client-side encryption guarantees message privacy
By distributing responsibility intentionally, we eliminate single points of failure and prevent sensitive data exposure through misconfiguration or over-privileged systems.
Technology Stack Used
Each layer of the stack was selected to support adherence, scalability, and long-term maintainability.
Frontend
- Next.js
- Firebase SDK
The frontend handles user interaction, secure session handling, and client-side encryption and decryption. Sensitive message content is encrypted before it ever leaves the device.
Backend
- NestJS
NestJS acts as the authoritative control layer of the system. It enforces:
- Role-based access control
- Business rules
- Consent validation
- Secure session coordination
No client can bypass backend authorization logic.
Database
- Firebase Firestore
Firestore functions as a “blind” data store. It stores only encrypted ciphertext and has no ability to read or interpret message content. Even if database access were compromised, message data would remain unreadable.
Identity & Authentication
- Google Identity Platform
Google Identity Platform provides enterprise-grade authentication covered under a Business Associate Agreement (BAA). It ensures:
- Secure user identity verification
- Strong authentication flows
- Regulatory-aligned identity management
| Layer | Technology | Key Role |
| Frontend | Next.js, Firebase SDK | Manages UI, secure sessions, and client-side encryption before data leaves the device. |
| Backend | NestJS | Enforces role-based access, business rules, consent checks, and secure session control. |
| Database | Firebase Firestore | Stores only encrypted ciphertext as a blind data store with no message visibility. |
| Identity & Auth | Google Identity Platform | Provides secure user authentication and identity management. |
Core Features of the PoC
The PoC was designed to reflect real-world healthcare workflows while enforcing strict security boundaries.
One-to-One Secure Physician-Patient Chat
- Direct private communication channels
- No group exposure or third-party visibility
- Messages visible only to the intended physician and patient
This ensures confidentiality at the conversation level.
Admin-Verified Practitioner & Patient Onboarding
All users are verified before gaining access.
- Admin manually creates and verifies practitioner accounts
- Admin manually creates and verifies patient accounts
- Eliminates impersonation and unauthorized access
This step is critical for maintaining trust and authenticity within the system.
Role-Based Access Control (RBAC)
The platform enforces clearly defined roles:
- Admin
- Practitioner
- Patient
Each role has strictly limited permissions. Users can only access actions and data explicitly allowed for their role, preventing accidental or malicious access to sensitive health information.
True End-to-End Encrypted Messaging (Zero-Knowledge Privacy)
Messages are:
- Encrypted on the sender’s device
- Transmitted securely as encrypted data
- Stored in Firestore as ciphertext
- Decrypted only on the recipient’s device
At no point can the platform, database, or backend services read message content. This enables true zero-knowledge privacy.
How the PoC Works
Below is the operational flow that ensures security and adherence at every stage.
Healthcare-Grade Cloud Infrastructure
- Business Associate Agreement (BAA) signed with Google
- Only eligible cloud services are used
- Security, encryption, and policies are configured upfront
This establishes a compliant foundation before any data is handled.
Admin User Onboarding
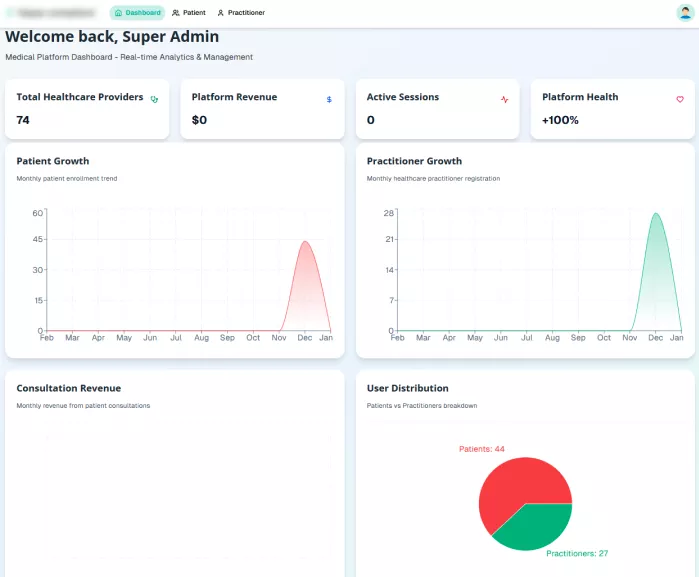
- Admin creates and verifies practitioner accounts
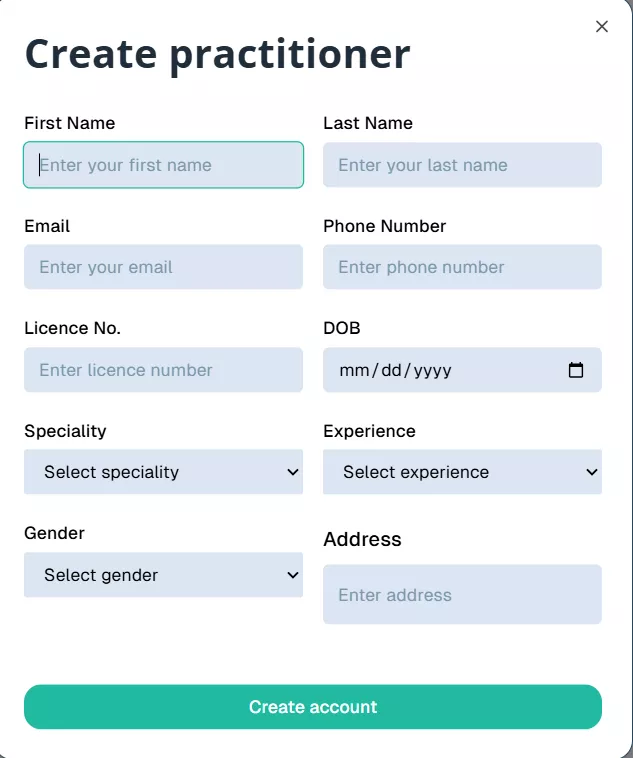
- Admin creates and verifies patient accounts

- Roles and permissions are explicitly assigned
No user enters the system without administrative approval.
Secure Authentication & Access
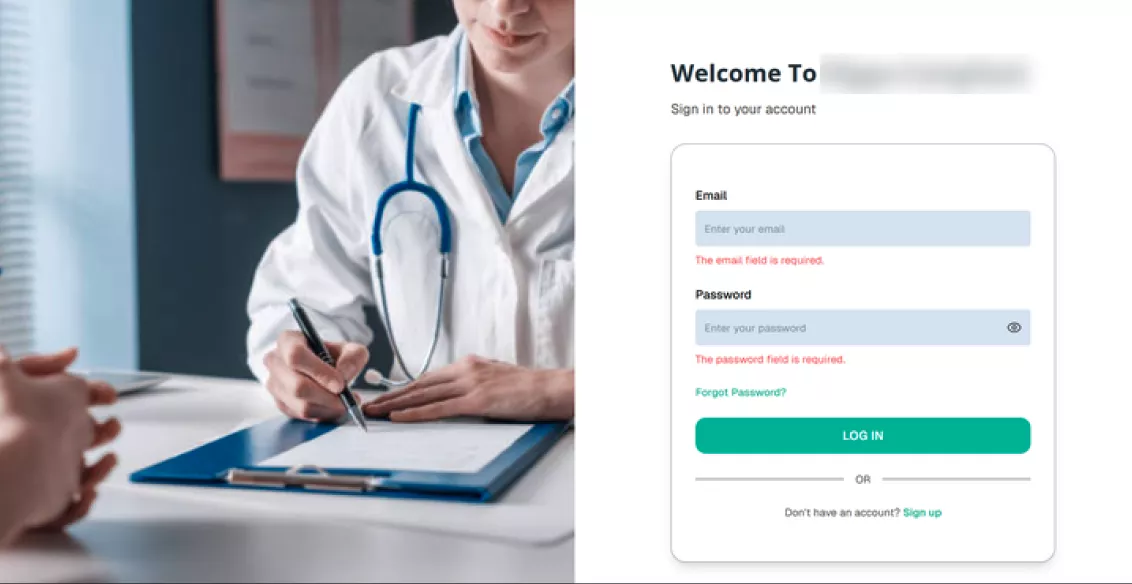
- Users authenticate through secure identity services
- Sessions are validated and scoped by role
- After a successful login, patients land on a protected dashboard
Unauthorized access is blocked at multiple layers.
Chat Session Initiation
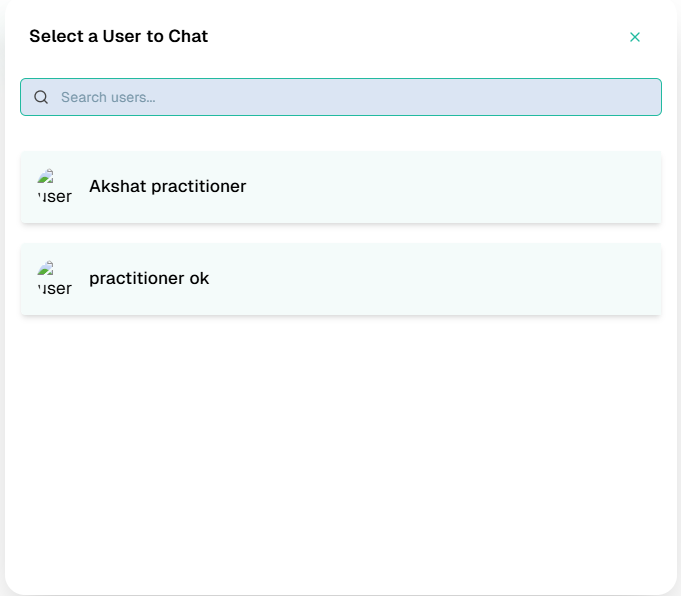
- Patient selects a verified practitioner
- A secure, authorized chat session is established
- Backend validates permissions before allowing communication
End-to-End Encrypted Messaging
- Messages are encrypted on the sender’s device
- Encrypted payload is transmitted securely
- Ciphertext is stored in Firestore
Message Decryption
- Only the intended recipient can decrypt the message
- No third party, including the system itself, can access message content
This guarantees privacy even in internal system operations.
Compliance Logging & Monitoring
- All access events and system activities are logged
- Audit logs capture behavior without exposing PHI
- Enables traceability and accountability
Data Retention & Disposal
- Messages are retained based on defined policies
- PHI is securely archived when required
- Data is permanently deleted when no longer needed
Lifecycle management is enforced as a system rule, not a manual process.
Ongoing Compliance & Security
- Regular security audits
- Continuous monitoring
- Ongoing adherence to healthcare security and privacy requirements
Adherence is treated as an ongoing responsibility, not a one-time setup.
Why This Approach Works
This PoC proves that Firebase can be used in regulated healthcare environments, when paired with the right architecture.
By combining:
- Shared responsibility
- Authoritative backend control
- Zero-knowledge encryption
- Structured data governance
Bitcot’s solution delivers secure, scalable healthcare communication without compromising privacy or adherence.
Bitcot’s Process Behind Building a Healthcare Secure Messaging Platform
Building a secure healthcare messaging platform requires more than technical expertise; it demands a disciplined, repeatable process that embeds adherence, privacy, and security into every layer of the system.
For this PoC, we followed a structured checklist to ensure that sensitive healthcare data is handled correctly from day one. Each step was intentional, verifiable, and designed to scale as the platform grows.
Below is the process we followed to meet healthcare regulatory requirements while using Firebase Firestore for a healthcare chat application.
Business Associate Agreement (BAA) with Google
The foundation of any compliant system starts at the infrastructure level.
We ensured adherence by executing a Business Associate Agreement (BAA) with Google. This formally defines responsibilities for the secure handling of PHI across Google Cloud, Firebase, and related services.
By establishing this agreement upfront, we ensured that all eligible services used in the platform meet healthcare regulatory requirements.
Comprehensive Data Encryption Strategy
Protecting sensitive healthcare data requires encryption at multiple levels.
We implemented:
- Encryption at rest to secure stored data
- Encryption in transit to protect data as it moves across the network
- Additional end-to-end encryption (E2EE) for chat messages
With end-to-end encryption in place, message content is encrypted on the sender’s device and decrypted only on the recipient’s device. This ensures maximum privacy and prevents unauthorized access, even from internal systems.
Secure Authentication and Access Control
Access to patient information must be tightly controlled.
We implemented strong authentication mechanisms combined with role-based access control (RBAC) to ensure that only authorized users can access relevant data. Each role, admin, practitioner, and patient, has clearly defined permissions enforced by backend logic.
This approach prevents privilege escalation, limits exposure to sensitive information, and ensures that users can only perform actions appropriate to their role.
Audit Logs and Continuous Monitoring
Accountability is a core requirement for healthcare systems.
We enabled comprehensive audit logging to track system access, authentication events, and key user actions. These logs provide full traceability while deliberately excluding sensitive message content, ensuring visibility without compromising privacy.
Continuous monitoring allows the platform to support compliance audits, detect anomalies, and respond quickly to potential security incidents.
Data Retention and Secure Disposal Policies
Healthcare data cannot be stored indefinitely.
We defined clear data retention rules that specify how long PHI is stored, when it should be archived, and when it must be permanently deleted. Secure deletion mechanisms were implemented to ensure that PHI is removed safely and irreversibly when it is no longer required.
By formalizing data lifecycle management, we prevent over-retention and reduce long-term compliance risk.
User Privacy and Consent Management
Patient privacy is not optional; it must be enforced at the system level.
We implemented explicit user consent flows and strict data access restrictions to ensure that patient data is only accessed and processed with proper authorization. Consent logic is centralized and consistently enforced across the platform, reducing the risk of fragmented or inconsistent privacy handling.
This structured approach ensures that patient privacy expectations are met throughout the entire user journey.
Regular Security Audits and Penetration Testing
To maintain long-term security and regulatory alignment, we incorporated ongoing security audits and periodic penetration testing into the platform lifecycle.
These assessments help identify vulnerabilities early, validate existing controls, and ensure that the system continues to meet evolving security standards.
By treating security as an ongoing process, the platform remains resilient as threats and requirements change.
A Repeatable, Adherence-First Blueprint
This process ensures that adherence is not bolted on after development, but built directly into the architecture, workflows, and operations of the platform.
The result is a healthcare secure messaging solution that:
- Protects PHI at every stage
- Scales without introducing compliance debt
- Provides auditability without sacrificing privacy
- Maintains trust between patients and providers
This same checklist-driven approach can be reused and adapted for future healthcare communication platforms.
Key Outcomes Delivered by Our Healthcare Secure Messaging Solution
A successful healthcare messaging platform is measured not just by how it’s built, but by the confidence it creates for the people who rely on it every day.
Our PoC was designed to deliver tangible outcomes for healthcare organizations, practitioners, and patients alike.
Below are the key results this secure messaging solution enables.
Increased Trust and Confidence Through Strong Security
Security and regulatory alignment are foundational to trust in healthcare communication.
By embedding security and adherence into every layer of the platform, the solution establishes confidence for both patients and practitioners. Patients can communicate openly knowing their information is protected, while healthcare providers can rely on the platform without concern over data exposure or misuse.
This trust is essential for adoption, engagement, and long-term platform success.
Scalable Growth Without Compromising Security
The shared-responsibility architecture ensures that the platform can scale safely as usage grows.
Rather than relying on a single service to handle all security and governance requirements, responsibilities are distributed across infrastructure, backend logic, and client-side controls. This approach allows the platform to grow in user volume, message traffic, and feature complexity without introducing security or compliance risk.
Scalability is achieved without sacrificing control.
Verified User Access Through Admin-Controlled Onboarding
User authenticity is critical in healthcare environments.
Admin-controlled onboarding ensures that only verified practitioners and patients can access the system. Every account is intentionally created and approved, eliminating impersonation risks and preventing unauthorized users from entering the platform.
This controlled access model reinforces trust and maintains the integrity of patient-provider communication.
Strict Role-Based Access to Sensitive Data
The platform enforces clear role-based access control across all users.
Admins, practitioners, and patients each have strictly defined permissions, ensuring that users can only access data relevant to their role. This minimizes unnecessary exposure to sensitive information and prevents accidental or malicious access.
Role enforcement is handled by authoritative backend logic, making access control consistent and auditable.
Complete Message Privacy Through End-to-End Encryption
All messages are protected with true end-to-end encryption.
Message content is encrypted on the sender’s device and decrypted only on the recipient’s device. At no point can the platform, backend services, or database read message content. This guarantees complete privacy and enables a true zero-knowledge communication model.
As a result, sensitive healthcare conversations remain confidential at all times.
Partner with Bitcot to Build Your Healthcare Secure Messaging Platform
Building healthcare software requires more than technical execution; it requires a partner who understands responsibility, risk, and long-term impact.
At Bitcot, we don’t approach healthcare projects as one-off builds. We approach them as systems that must earn trust, stand up to scrutiny, and scale without breaking. That mindset is what sets us apart.
We Don’t Start From Scratch; We Start From Proven Architecture
One of the biggest advantages of working with Bitcot is our blueprint-driven approach.
We’ve already engineered the core architecture for secure healthcare messaging, covering encryption, access control, auditability, identity, and data governance. This means we’re not experimenting on your product or rediscovering known challenges.
Instead, we begin with a proven foundation and focus our energy on adapting it to your exact use case.
Faster Time to Market Without Cutting Corners
Because our foundational architecture is already in place, we’re able to move significantly faster than teams starting from a blank slate.
This doesn’t mean shortcuts; it means efficiency. Security, adherence, and scalability are built in from day one, allowing your team to:
- Launch faster
- Validate ideas sooner
- Reduce go-to-market risk
Speed and responsibility don’t have to be opposites.
Cost-Efficient Without Compromising Quality
Healthcare platforms are expensive to build when every problem is solved from scratch.
Our blueprint approach reduces redundant development effort, which translates directly into cost savings. You get a high-quality, enterprise-grade solution without the inflated timelines or budgets often associated with regulated software development.
It’s a smarter investment, not a cheaper one.
Custom Solutions, Not Cookie-Cutter Products
While our architecture is proven, every solution we deliver is fully customized.
We tailor:
- User flows
- Roles and permissions
- Feature sets
- Integrations
- UI and product behavior
Your platform reflects your product vision, your users, and your workflows, supported by a secure foundation designed to adapt, not constrain.
A Partner Who Understands Healthcare Realities
Healthcare technology operates in a world where mistakes carry real consequences.
Our team understands the balance between usability, security, and operational practicality. We design systems that make sense for real clinicians, real patients, and real product teams, not just theoretical requirements.
That perspective helps avoid overengineering while still meeting the standards healthcare demands.
Built for Long-Term Growth, Not Just Launch Day
We design platforms with the future in mind.
As your product grows, adds users, or expands functionality, our architecture supports that evolution without introducing fragility or technical debt. This long-term thinking helps you avoid costly rewrites and painful migrations later.
Final Thoughts
Building a healthcare messaging platform isn’t just a technical challenge; it’s a trust challenge, ensuring strong security, privacy, and trust.
For patients, it’s about feeling safe enough to share personal information without worrying about who might see it. For practitioners, it’s about having a reliable communication tool that doesn’t introduce risk or uncertainty into their daily workflows. And for product teams, it’s about finding the balance between moving fast and building responsibly.
Secure, privacy-first communication isn’t just a technical requirement anymore; it’s a foundational pillar of modern healthcare digital transformation.
What this PoC demonstrates is that you don’t have to choose between scalability and security, or between modern tools and regulated requirements. With the right architecture, Firebase can be part of a secure, privacy-first healthcare messaging solution that grows confidently over time.
The key is intention.
Security, access control, encryption, and data governance can’t be afterthoughts. When they’re designed into the system from the start, they become strengths instead of constraints.
At Bitcot, this is exactly how we approach healthcare technology. We specialize in building Firebase Firestore-based chat applications that are practical, scalable, and aligned with real-world healthcare needs, not just theoretical compliance checklists.
Whether you’re launching a new product or rethinking an existing system, our team brings deep experience in custom healthcare development services that prioritize both usability and trust.
If you’re exploring secure healthcare communication or need a partner who understands how to build regulated systems the right way, we’d love to help.
Let’s turn complexity into clarity, and ideas into secure, production-ready solutions. Get in touch with our team.












